Cybersecurity
- Home
- Cybersecurity
 The ProSpace Platform
The ProSpace Platform
Meet Modular Cybersecurity
Meet Modular Cybersecurity: tailored, flexible security solutions designed to protect your cannabis business from digital threats, ensuring compliance and safeguarding sensitive data. Adaptable and robust.
Modules for Protecting Endpoints
- Endpoint Security
- Endpoint Detection and Response
- Endpoint Data Governance
- Wifi Phishing
- Mobile Device Management
Modules for Protecting Email and Users
- Email Security
- User Data Governance
- Secure Messages
- Inbound Gateway
Modules for Protecting Network and Cloud Environments
- Network
- Cloud Security
- Secure Web Gateway
- Zero Trust Network Access
 The ProSpace Platform
The ProSpace Platform
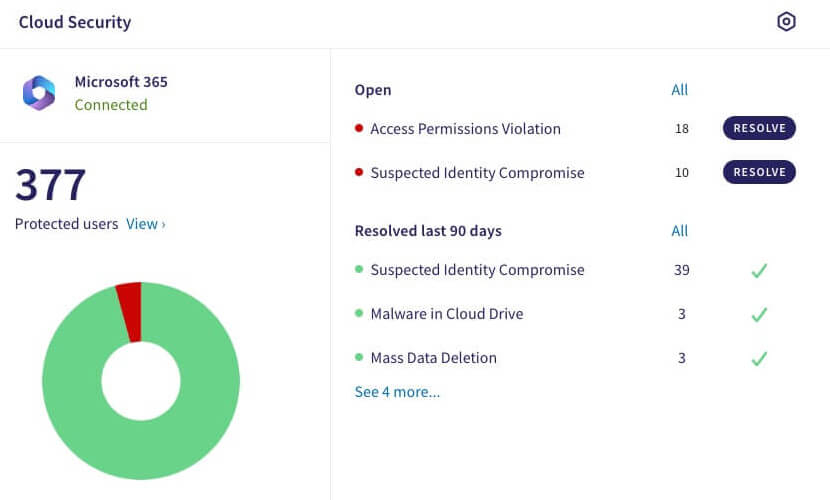
One Dashboard for Everything
Unlike typical reporting interfaces, ProSpace's dashboard lets you click into modules to resolve any tickets ProSpace hasn't already handled for you.
One Unified Agent for Every Module
With ProSpace Cannabis, say goodbye to manual maintenance, updates, and conflicts among multiple agents. Our single endpoint agent integrates device posture, next-gen antivirus, EDR, VPN, data governance, firewall, and DNS filtering. Adding modules triggers automatic updates based on your defined rules, across Windows, Windows Server, and Mac OS.

 Our Services
Our Services
A Growing Collection of Security Modules
Access Management
Ensure secure access to resources by managing user identities and access privileges.
Cloud Security
Protect assets hosted on platforms like AWS and Azure and cloud access security broker (CASB).
Endpoint Security
Protecting individual devices (endpoints), encompassing antivirus and anti-malware solutions.
Incident Response
Help organizations prepare for, respond to, and recover from cybersecurity incidents.
Managed Security
Encompass outsourcing various security functions to third-party providers.
Mobile Device Security
Focus on securing mobile devices and applications used within an organization.
Network Security
Focus on safeguarding an organization's network infrastructure from cyber threats.
Risk Management
Managing cybersecurity risks and complying with industry regulations and standards.
Security Awareness
Educate employees about cybersecurity best practices and risks in recognizing threats.
Security Consulting
Expert guidance to organizations in creating robust cybersecurity strategies.
Security Information
Collecting and analyzing data from various sources to provide real-time threat monitoring.
Vulnerability Assessment
Vulnerability scanning assesses system works, while penetration testing involves ethical hacking.